Common types of attack vectors
- Compromised credentials
- Weak and stolen credentials
- Malicious insiders
- Misconfiguration
- Vulnerabilities
- Malware
An attack vector can be classified as either:
- Active attack vector
- Passive attack vector
Active attack vector
Active attack vectors affect the integrity and availability of information. An attacker tries to alter or modify a system through malware, exploiting vulnerabilities, man–in–the–middle attacks and ransomware.
In the figure below, an attacker captures the message from the sender and changes its contents before sending the misleading message to the receiver.
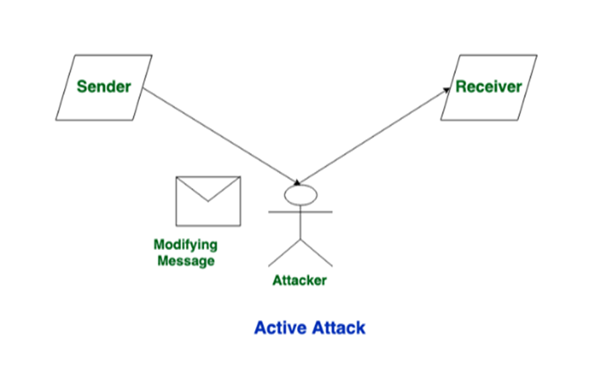
Active attacks are in the form of:
- Interruption – An attacker tries to deny users access to the system
- Modification – An attacker captures a message and alters its contents
- Fabrication – An attacker inserts fake information, resources or services into the network
Types of Active Attacks
Masquerade
A threat actor or attacker impersonates a legitimate user to gain unauthorized access to network resources. The main goal is identity and data theft.
In the image below, Darth is sending a message to Alice that appears to be from Bob. Darth, who is an illegitimate user, is masquerading as Bob.
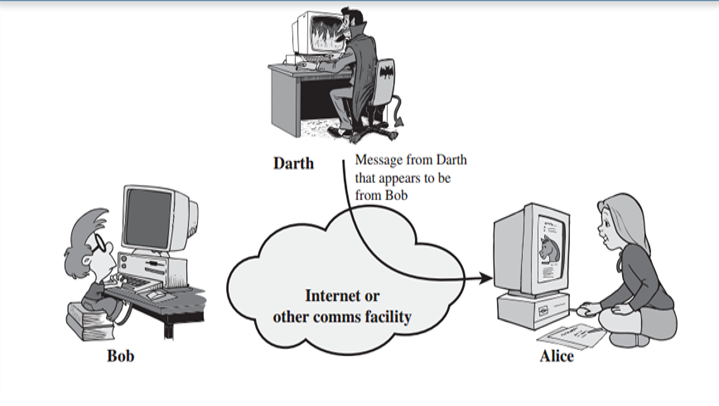
Repudiation
A user can deny having executed a certain action or initiated a malicious transaction that caused a loss. Repudiation can be by the sender or receiver.
For example, a student can use the school computer to access a malicious website causing a cyber–attack. The student then denies accessing the websites as he or she knows it is against school guidelines.
Replay
A threat actor eavesdrops on secure network communication, intercepts it then fraudulently delays or resends it to misdirect the receiver into doing what the hacker wants. In the image below, Darth (attacker) intercepts the message from Bob (sender) to Alice and changes its contents before redirecting it to the intended receiver Alice.
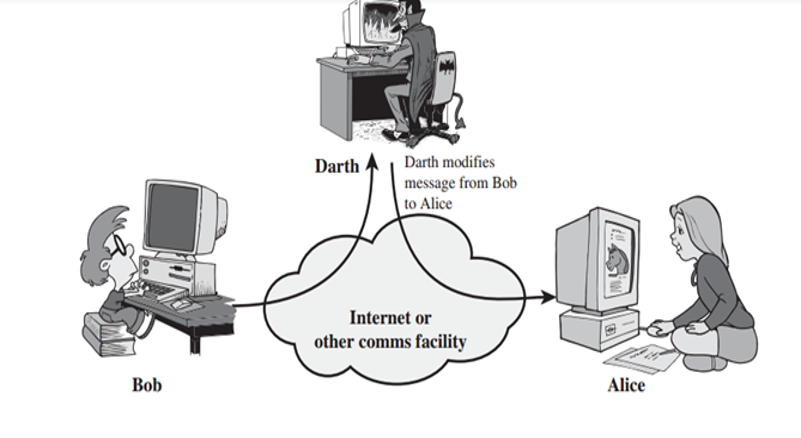
Denial of Service
An attacker prevents a legitimate user from accessing network resources such as a school management system or student portal. An attacker floods the server with traffic or sends an action through code to cause a crash.
In the image below, Darth (attacker) interrupts Bob, who is a legitimate user from accessing services provided by the server.
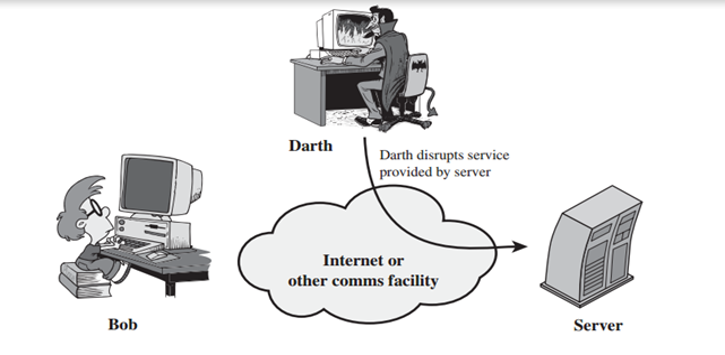
Passive attack vector
Passive attacks are a threat to data confidentiality. An attacker strives to gain access or gather information about the target without altering the system resources.
The figure below explains how a passive attack occurs. An attacker reads the message from a sender to a receiver without modifying its contents.
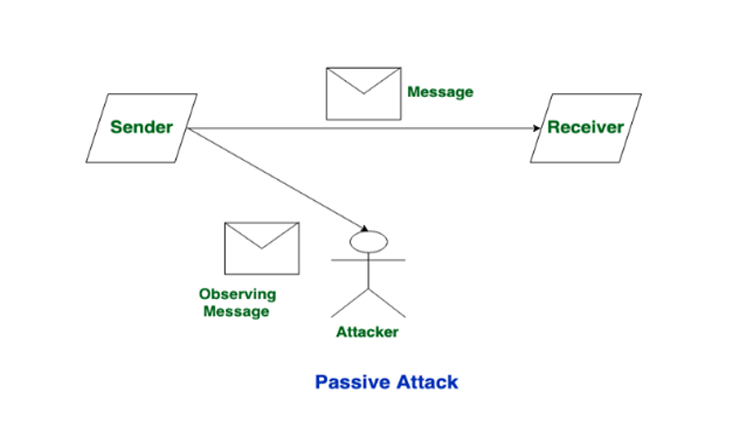
Types of Passive Attacks
Message Release
An attacker monitors the contents of data in transmission. The information could be in the form of a telephonic conversation, an e–mail message or a transferred file.
Traffic Analysis
Passive attacks can be conducted through various social engineering attacks
Dumpster diving
An attacker goes through abandoned computers, devices or trash bins to try and acquire information from them. To prevent this, always shred documents and format devices that are no longer in use.

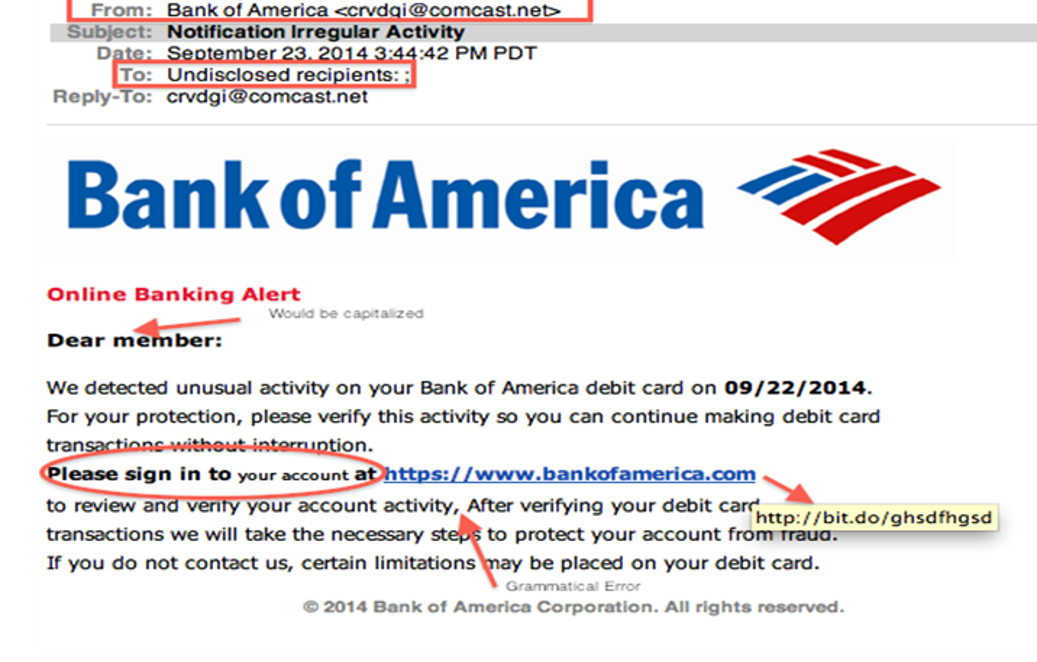
Phishing
An attacker can use SMS, e–mails or web advert to try and trick a user into giving sensitive information or visit a malicious website.
Baiting
This involves luring a user with an offer such as branded corporate branded flash disks in exchange for private information.

Piggybacking / Tailgating
This is when an unauthorized person physically follows an authorized person into a restricted corporate area, for example, a building or server room.

Pretexting
An attacker tries to persuade a user into giving sensitive information by providing a fictional backstory. The image below shows examples of pretext social engineering.

Similarities between active and passive attack vectors
- An attacker identifies a potential target
- An attacker collects information about a target using social engineering, malware or phishing
- Information acquired is used to identify possible attack vectors and create or use tools to exploit them
- Attackers gain unauthorized access to the system and steal sensitive data or install malicious code
- Attackers monitor the computer or network, steal information or use computing resources
Difference between Active and Passive attack vector
| Active Attack Vector | Passive Attack Vector |
| A threat to the integrity and availability of the data | A threat to data confidentiality |
| Accomplished by gaining the physical control over the communication link to capture and insert transmission | The attacker requires to observe the transmission |
| Involves a modification of data | Involves the monitoring of data |
| The victim is aware of the attack | The victim is unaware of the attack |
| Affects the system and is easily detected | It does not affect the system and is not easily detected |
| Difficult to prevent the network from active attack | It can be prevented |
- Training of staff and students
- Apply the Principle of Least Privilege where a user is given minimal access rights to perform the needed task. A student can be granted permission to access the internet using kid friendly search engines only.
- Use cybersecurity tools such as firewalls, password managers and VPNs for secure communications
- Patch operating system and update device software to the latest version
- Encrypt sensitive information and data at rest, in–transit and in processing
- Monitor data and network access for all users and devices to unmask insider risk
- Use two–factor authentication via a trusted second factor to minimize the number of breaches

