Wireless and Mobile Device Attacks
Wireless Attacks
Wireless networks have made life easier, especially during the Covid-19 pandemic, whereby schools closed, and learning and teaching from home became the new norm. However, wireless networks are susceptible to attacks that can cause great harm to a device and the user. A wireless attack is a malicious action against wireless networks or wireless system information. An example is a rogue access point.
Common Wireless Vulnerabilities
A vulnerability is a weakness that can be exploited by a hacker to compromise a device or network. Below is a list of common weakness a threat actor can take advantage of:
Default SSIDs and Passwords
SSID (Service Set IDentifier) is the name used to identify a wireless network before connecting. The image below shows Wi-Fi networks available under different SSIDs or Wi-Fi name.

Wi-Fi devices such as access points and home routers come with default credentials. Depending on the brand, default credentials are the same across these devices. This makes it easy for an attacker to compromise a wireless network by logging in and taking over the router, loading malicious scripts or redirecting network traffic to a their server. An attacker can steal user information such as bank details or the identity of a user, and use it for fraudulent activities or sell it in the dark web. Default usernames and passwords must be changed immediately to prevent a hacker from accessing the wireless network.
Access Point Location
An access point should not be in a place where it is easily accessible. An attacker, in a matter of seconds, can revert the access point to default settings and set the configurations to redirect traffic to him.
Wired Equivalent Privacy (WEP) Protocol
WEP is a wireless traffic encryption protocol that has been deprecated; hence it is no longer secure. Through the use of tools, an attacker can easily crack the password or reverse the encryption process and view information in the wireless network. A user should instead use Wi-Fi Protected Access 2 (WPA2) or Wi-Fi Protected Access 3 (WPA3) encryption protocols that are more secure.
Types of Wireless Attacks
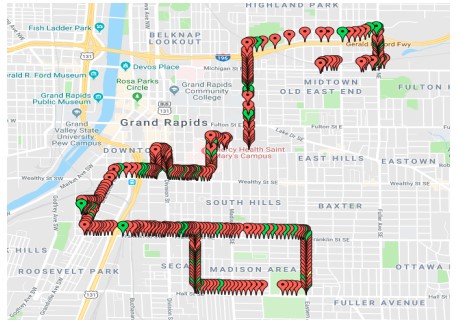
War-driving
It is also referred to as access point mapping. This is the act of looking for wireless networks by moving around a town or city using a GPS device while recording the location of wireless networks. The information is then uploaded to a website to digitally map the networks in that area.

An example of War-driving mapping
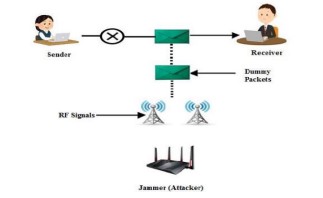
Jamming
This can also be referred to as network interference. Its main intention is to disrupt the network. Objects such as Bluetooth headphones, microwave and walls can cause interference when a user tries to connect to Wi-Fi. An attacker can combine jamming techniques to intentionally cause network interference. A spectrum analyser will prevent jamming by boosting the signal strength of the access points. A user can also set up the router to use different frequencies, 2.5 GHz and 5 GHz.
Rogue Access Points
A rogue access point is an unauthorized access point that an individual has set up without informing the network administrator. A wireless access point is easy to install. Using a Windows machine, a user can create a wireless network. However, these access points are not protected hence can easily be hacked or an attacker can create one to entice valid users away from their corporate network and capture the traffic.
Two high school students in New Jersey, hacked into the school Wi-Fi and brought down all the network services. The attack paralyzed all online activities in the school. The staff could not access the school systems, and the students could not access their work and classes. The two students conducted the hack simply because they did not want to sit for an exam.
Videos demonstrating the dangers of connecting to insecure Wi-Fi network:
- Hacker Demonstrates Security Risks Of Free Public Wi-Fi
- What happens when you connect to an unsecured public Wi-Fi network?
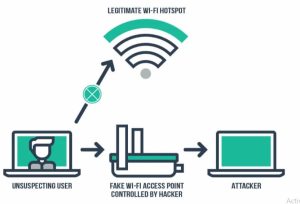
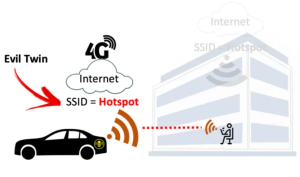
Evil Twin Access Points
This is an illicit wireless access point that appears genuine but is set up to eavesdrop on wireless communications. An attacker can use a malicious website and steal their information and take over their computers.
Video demonstration of an evil twin access point.
Packet capturing and sniffing
An attacker captures incoming and outgoing packets in the network traffic and reads information sent between the sender and the receiver. Most information sent is in plaintext, and no form of encryption is in use. Through packet capture analysis, a threat actor can acquire sensitive information such as passwords, usernames and credit card information. There are tools used for this including Wireshark, Ettercap, BetterCAP, Tcpdump and WinDump.

War shipping
This comes from the term ‘package shipping’ which is common in online shopping websites such as eBay, Amazon or Jumia. An attacker sends a package with malicious hardware to the physical address of a target, for example, school premises or home using shipping services. The hardware is remotely accessed by the attacker and used to orchestrate an attack.

Wireless Attacks Scenarios
- A 12-year-old student in Baker County Middle School hacked the school’s Wi-Fi because he did not want to go to school. The student shut down the school’s phone lines and internet.
https://www.firstcoastnews.com/article/news/education/baker-co-student-could-face-felony-forreportedly-hacking-schools-wifi-to-avoid-doing-school-work/77-046439b4-e8c8-4b95-b847-ea0d455c91a3 - Amazon CEO Jeff Bezos’ phone was allegedly hacked by a Saudi Crown Prince in 2018. https://www.businessinsider.com/jeff-bezos-phone-hacked-whatsapp-security-experts-2020-1?IR=T
- Colleges are turning students’ phones into surveillance machines, tracking the locations of hundreds of thousands.
https://www.washingtonpost.com/technology/2019/12/24/colleges-are-turning-students-phonesinto-surveillance-machines-tracking-locations-hundreds-thousands/ - Russian agents camped outside hotels to try hack victims remotely.
https://www.wired.com/story/russian-spies-indictment-hotel-wi-fi-hacking/
- Users should avoid using untrusted networks especially public Wi-Fi
- Ensure your devices have the latest software update
- Enable a firewall or VPN to protect your information
- Use strong and unique passwords for your network
- Turn off the wireless home network when you are not at home
- Disable Remote Access
Mobile Device Attacks
What do your mobile devices know about you?
Mobile devices have become an important part of our lives because they make work easier. We use mobile devices to conduct financial transactions, teach or learn online, access websites, government platforms, browse social media platforms, download private files and so on. This means that our devices know almost everything about us. For instance, if you lose you smartphone and a malicious person gets hold of it, they are able to access your passwords, social security information, files, passwords, messages, emails, addresses, location information, web history and banking information. The person can further impersonate you by stealing your identity and committing a crime.
What are mobile device attacks?
A mobile device attack is an exploit targeting handheld or portable communication devices such as a cell phone, smartwatch, Bluetooth headset, laptops and tablets.1 Most educators and learners use smartphones and laptops during online classes.
Types of mobile threats
App-based
Applications available in platforms such as play store and App-Store have made the smartphone experience better. However, it is difficult to detect a malicious app because it may look genuine on a download site. A legitimate application can also be exploited for fraudulent intentions.
Web-based
Mobile devices can connect to the internet and access web services such as banking services, school websites, staff portal and learning management systems. When a user visits a malicious site, malware can be automatically downloaded to the device without the user’s knowledge.
Network-based
Mobile devices support Wi-Fi and Bluetooth technologies. An attacker can take advantage of this when a user leaves the Bluetooth enabled or connects to an unsecured Wi-Fi network and installs malware. An attacker makes use of any weakness present in an application or operating system (Windows, Android or iOS) to install harmful code.
Physical
This involves the loss of a mobile device to an attacker. Sensitive information in the phone is vulnerable as the attacker has full access to the physical device. A threat actor can also get into your institution’s network using your identity and cause havoc.
Effects of a mobile device attack
An attacker can:
- Listen to actual phone calls as they happen
- Secretly read SMS texts, capture call logs and emails
- Listen to the phone surroundings
- View the device’s GPS location
- Forward all email correspondence to another inbox
- Remotely control all phone functions via SMS
- Have total control of the mobile device
Types of mobile device attacks
Malware
Malicious software that targets devices such as laptops, smartphones and tablets with the aim of accessing sensitive data or taking control of the device. Examples are:
Adware
An attacker attempts to flood malicious and unwanted adverts to a user’s computer or smartphone’s. Adware can be used to collect data, redirect to malicious sites or change your browser’s settings. The danger of adware is that data collected can be sold in the dark market and used for identity theft.

Browser exploit
Mobile browsers are not completely safe. Therefore, an attacker can take advantage of its weakness and change browser settings without your knowledge. An example of an application that works in a browser and abuses this is PDF readers.

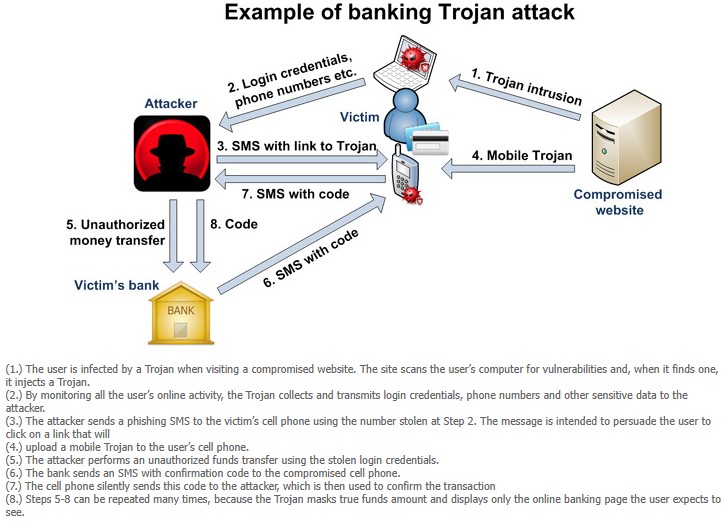
Trojan
It masks and presents itself as a legitimate entity. It is commonly used in SMS and applications whereby a user downloads an application thinking it is genuine only for their device to be compromised. Through SMS, an attacker sends a message to premium-rates numbers around the world using a user’s device without their knowledge. The user receives a message that they have subscribed to the service. The message is tied to the hacker who is able to intercept text messages, especially those in relation to financial information.
Spyware
Hackers use spyware to track the online activities of users without their knowledge or consent. It can spread easily by exploiting the weakness in a software application. It is able to acquire information through activity monitoring, collecting keystrokes (keyboard inputs) and harvesting of account information such as logins and financial data.

Phishing
A cyber-attack where an attacker tries to get information from a user by disguising as a trusted entity and tricks a user into giving sensitive information such as username and password. This can be done through an email, instant message, phone call or text message.
Clone phishing
An attacker uses a legitimate email message from a trusted source and alters it to fit his or her objective and appear like it is from the original source. He or she may add a malicious link or attachment that downloads a virus, compromising the user’s device.
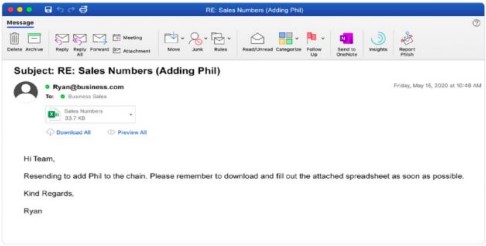
Email phishing
An attacker sends an email that is very convincing, sometimes containing a malicious link that downloads malware into the computer of the user or redirects them to a harmful website.
SMiShing
This attack uses Short Message Services (SMS) to send malicious or fraudulent texts or links. The attacker tries to acquire information when the user clicks on the malicious link. A user can also receive a text message that looks like it is from a trusted source, for example, a bank. The attacker, however, through the convincing text message is trying to trick you into providing confidential information.
Vishing
Also known as voice phishing. An attacker attempts to trick a person into giving up sensitive information by providing a convincing fictional story. This is conducted through phone calls using mobile phones or VoIP devices.

Bluetooth Exploits
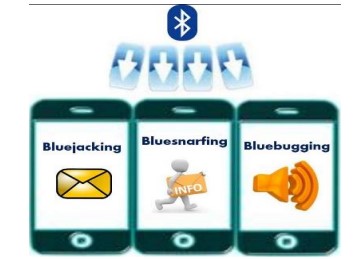
Bluejacking
This involves sending unsolicited messages to a Bluetooth enabled device in a certain range, usually 10 meters. The messages can be either texts, images, videos or audio. The attacker can only send messages but cannot extract data from your device.
Bluebugging
An attacker takes full control of a mobile device. He or she can listen in on phone conversations, enable call forwarding, send messages, access contact list and access applications.
Bluesnarfing
An attacker uses tools to attack a mobile device, gain access and steal data using Bluetooth without the user’s knowledge. Target data include International Mobile Equipment Identity (IMEI) to route a person’s incoming calls to their cell phones, bank details, calendar information or addresses.
Blue Borne
Blue Borne is an attack that gets into a device (Android, iOS, Linux or Windows) via Bluetooth and takes full control of the device. It affects computers, mobile phones, and IoT devices (smart cars and wearables). The attack does not require the targeted device to be paired to the attacker’s device, or set on discoverable mode. If your Bluetooth is on and you are in the vicinity of an already infected device, then the virus will get easily transferred to your device without asking for any permission.
- Keep your phone locked when not in use
- Use a secure application that encrypts communications such as Signal, WhatsApp, ChatSecure
- Set secure protection measures for your device such as complex patterns or passwords, fingerprint, or face recognition
- Keep your device’s OS up-to-date to the latest Android or iOS
- Connect to secure Wi-Fi networks only
- Beware of malicious downloads or links
- Encrypt your data using encryption tools such as ZealCrypt and Crypto
- Install anti-virus software for your device
- Install an advert blocking application such as Adblock Plus, Ad-Blocker and AdGuard
WhatsApp is currently the most used application for communication. Teachers around the globe use it to conduct online classes and pass information to students and their parents or guardians. You can secure your WhatsApp account through the following tips:
- Never share your registration code or two-step verification PIN with others
- Enable two-step verification and provide an email address in case you forget your PIN
- Set a device code
- Be aware of who has physical access to your phone (If someone has physical access to your phone, they can use your WhatsApp account without your permission)
How to enable two-step verification in your WhatsApp account
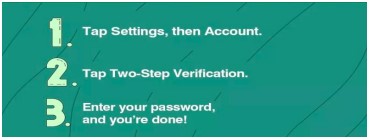
Additional Reading Material on WhatsApp Security
- https://www.howtogeek.com/658977/how-to-secure-your-whatsapp-account/
- https://www.timesnownews.com/technology-science/article/whatsapp-security-features-five-tipsto-keep-your-whatsapp-chats-safe-and-secure/593244
- https://indianexpress.com/article/technology/social/5-whatsapp-security-features-that-you-shouldenable-right-away-627796